Single Sign-On with Keycloak
RemotePC Team and Enterprise plan users can use Single Sign-On (SSO) for accessing their account. Admin of the accounts can choose a SAML 2.0 identity provider (IdP) to login to your RemotePC account without having to remember another password.
To setup Single Sign-On (SSO) with Keycloak, the admin needs to:
- Configure Single Sign-On (SSO) with Keycloak as IdP
- Add Users
- Configure RemotePC account for Single Sign-On (SSO)
To use Keycloak as an identity provider for SSO, you need to create a SAML 2.0 client.
To create a SAML 2.0 client,
- Login to the Keycloak Administration Console. Once you have logged in, you can see the Administration Console with a Master realm already present.
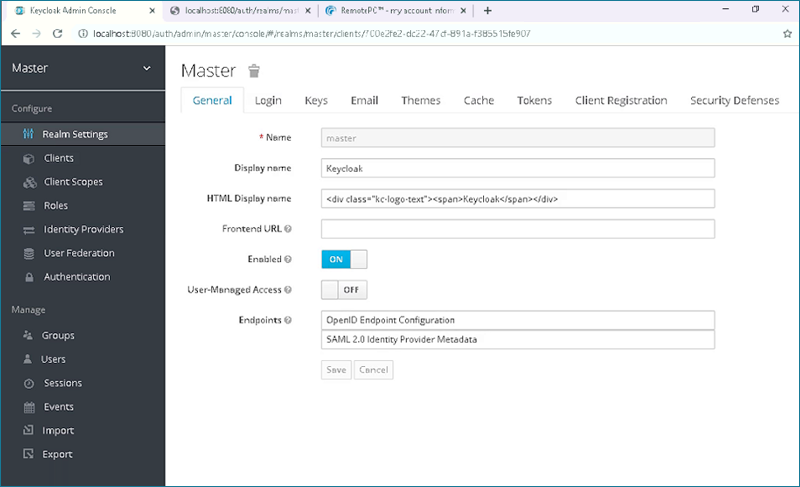
- Go to the 'Clients' tab, click 'Create' button on the right hand side of the page and add below URL:
Client ID: https://sso.remotepc.com/rpcnew/sso/metadata
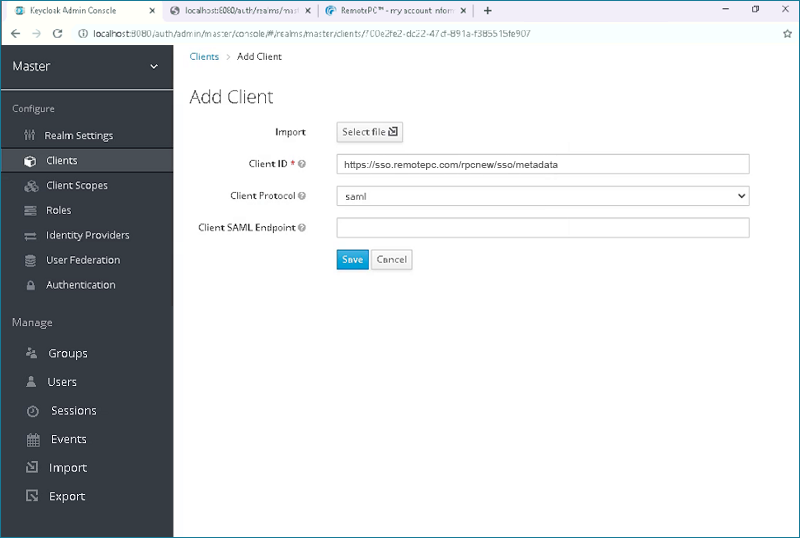
- Click on the 'Client Protocol' drop down box and select 'saml'.
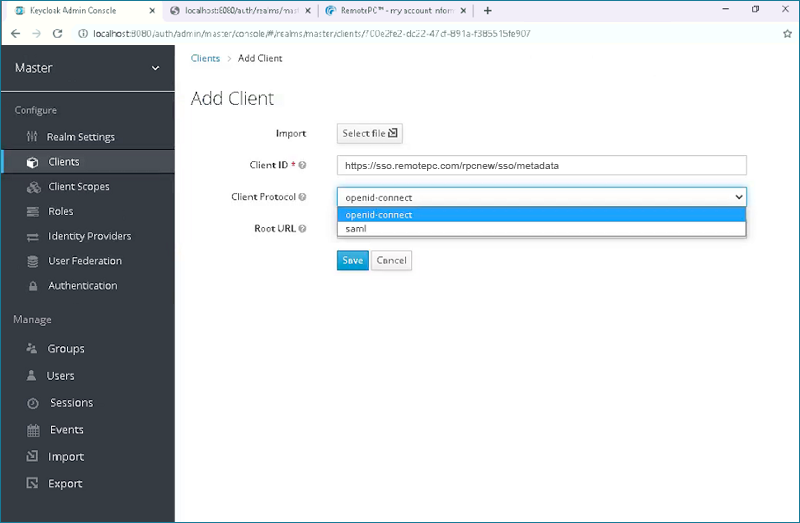
- Click 'Save'. This will create the client and automatically redirects you to the client Settings tab.
- In order to use Keycloak for SSO with RemotePC, we need to make few changes in the Keycloak client settings.
Modify the required changes as below:
- Client ID: https://sso.remotepc.com/com/rpcnew/sso/metadata
- Name: RemotePC
- Enabled: ON
- Consent Required: OFF
- Client Protocol: saml
- Include AuthnStatement: ON
- Include OneTimeUse Condition: OFF
- Sign Documents: ON
- Optimize REDIRECT signing key lookup: OFF
- Sign Assertions: OFF
- Signature Algorithm: RSA_SHA1
- SAML Signature Key Name: KEY_ID
- Canonicalization Method: EXCLUSIVE
- Encrypt Assertions: OFF
- Client Signature Required: OFF
- Force POST Binding: ON
- Front Channel Logout: ON
- Force Name ID Format: ON
- Name ID Format: email
- Valid Redirect URLs: https://sso.remotepc.com/rpcnew/sso/process
- Master SAML Processing URL: https://sso.remotepc.com/rpcnew/sso/process
- Assertion Consumer Service POST Binding URL: https://sso.remotepc.com/rpcnew/sso/metadata
- Assertion Consumer Service Redirect Binding URL: https://sso.remotepc.com/rpcnew/sso/metadata
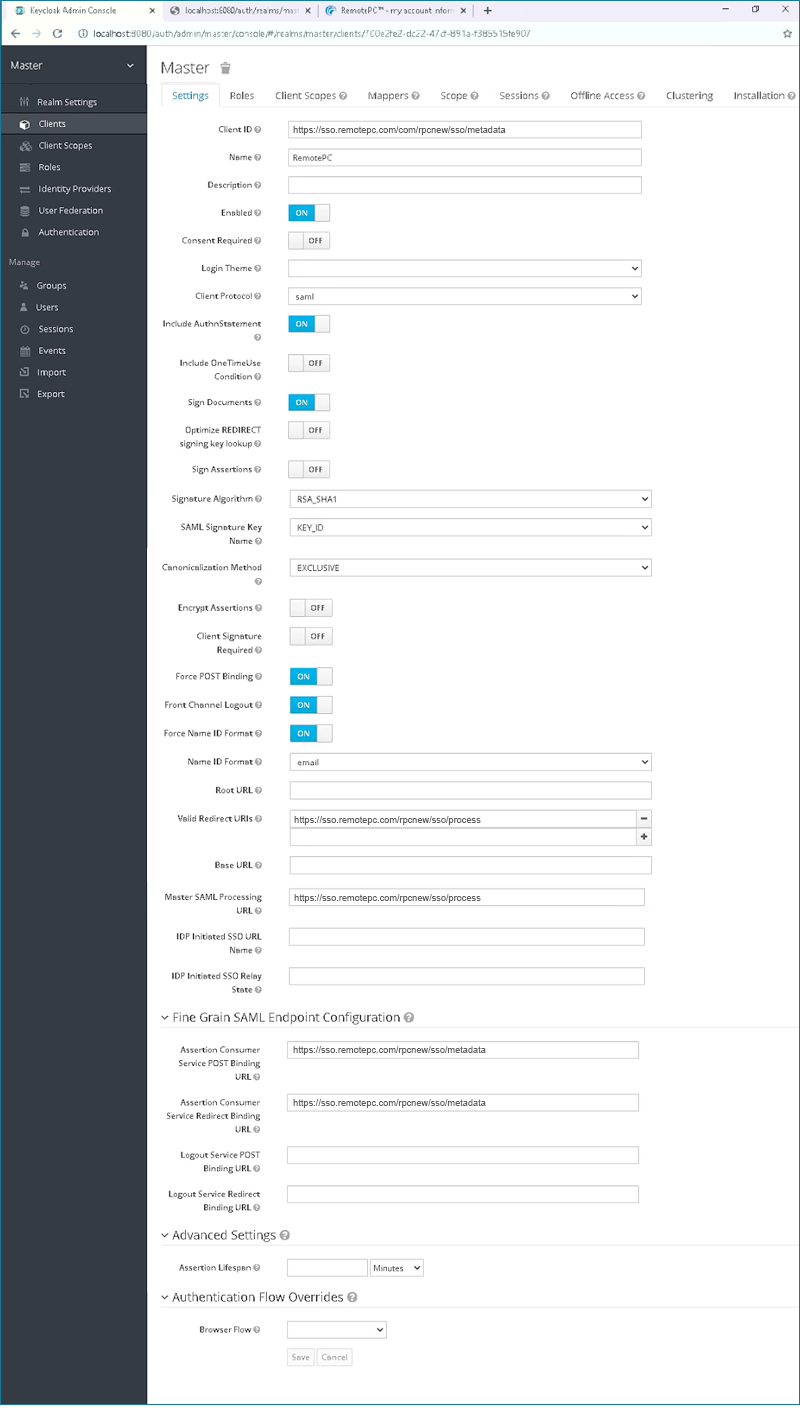
- Click 'Save'.
To enable SSO for user accounts, admin needs to add users to the SAML 2.0 client created on Keycloak Administration Console.
To add users,
- Go to the 'Users' tab and click 'Add user'.
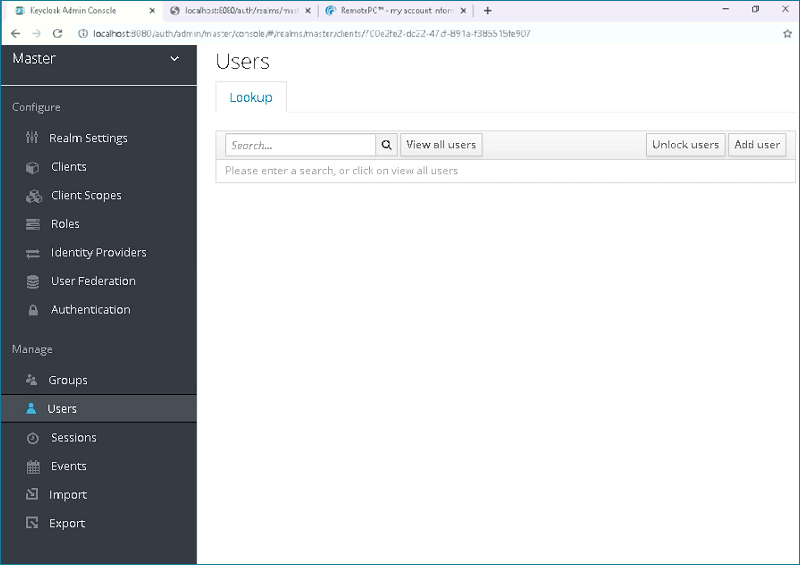
- Enter the 'Username', 'Email' and click 'Save'.
Note: The email address entered should match with the one, which you have provided to login with your RemotePC account.
- Once the user is created, go to the 'Credentials' tab and set a password for the user which will be used to login.
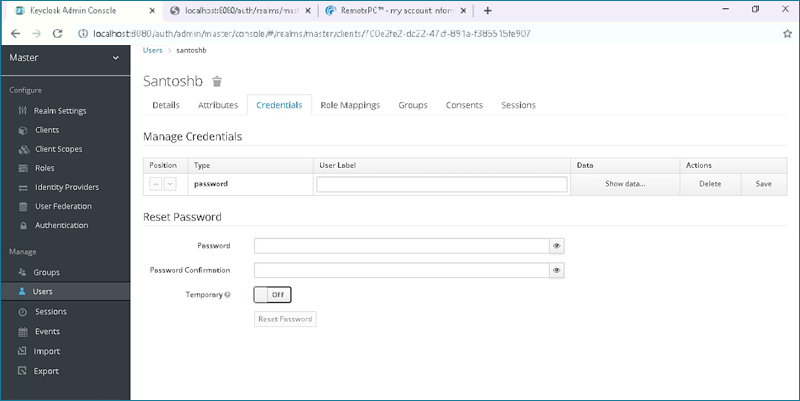
- Set the 'Temporary' toggle switch to 'OFF' and then click 'Set Password' to apply your changes.
Admin needs to provide the received SAML 2.0 URLs and Certificate in the Single Sign-On application from the RemotePC web interface.
To configure SSO,
- Login to RemotePC via web browser.
- Click the username displayed on the top-right corner and click 'My Account'.
- Click 'Single Sign-On'.
- Enter a name for your SSO profile and add below URLs:
- IDP Issuer URL:
http://localhost:8080/auth/realms/master
Eg: https://serverdomainname/auth/realms/master - Single Sign-On Login URL:
http://localhost:8080/auth/realms/master/protocol/saml
Eg: https://serverdomainname/auth/realms/master/protocol/saml
Note: URLs may vary depending on your installation of Keycloak. By default, Keycloak is installed on port 8080. If you have modified this or if your Keycloak installation exists on a different port, you will need to modify this URLs.
- IDP Issuer URL:
- Add the 'X.509 Certificate' received from your SAML 2.0 client, created on Keycloak Administration Console.
Note: To view and copy the X.509 Certificate,
i. Go to the 'Realm Settings' tab from your Keycloak admin console.
ii. Select the 'Keys' tab and click the 'Certificate' button on the right hand side of the page.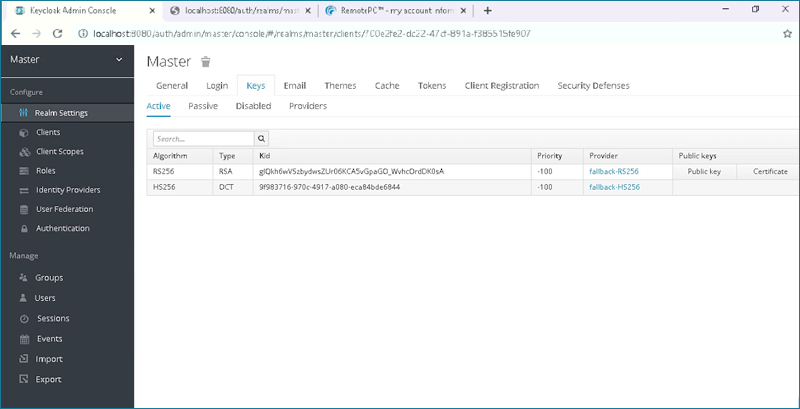
- Click 'Configure Single Sign-On'.
You will receive an email when SSO is enabled for your account.